DataMapper use best practise for data security
Data security is essential when using DataMapper. Your data is treated with the utmost respect, adhering to the highest standards of international data security.



We comply with Denmark’s Agency on Digitization’s best practices
We comply with the Danish government’s Agency on Digitization’s best practice guidelines for IT providers. To make it easy for you to learn about DataMapper security, we’ve published our answers to 11 questions the agency use to evaluate software here.
Key points:
- We log all access to your files.
- We frequently back up documents and data.
- We use the latest encryption standards both when transferring and storing your documents, including backup.
- We guarantee that your data does not leave the EU.
- We monitor and keep all servers up to date with the latest OS and security patches.
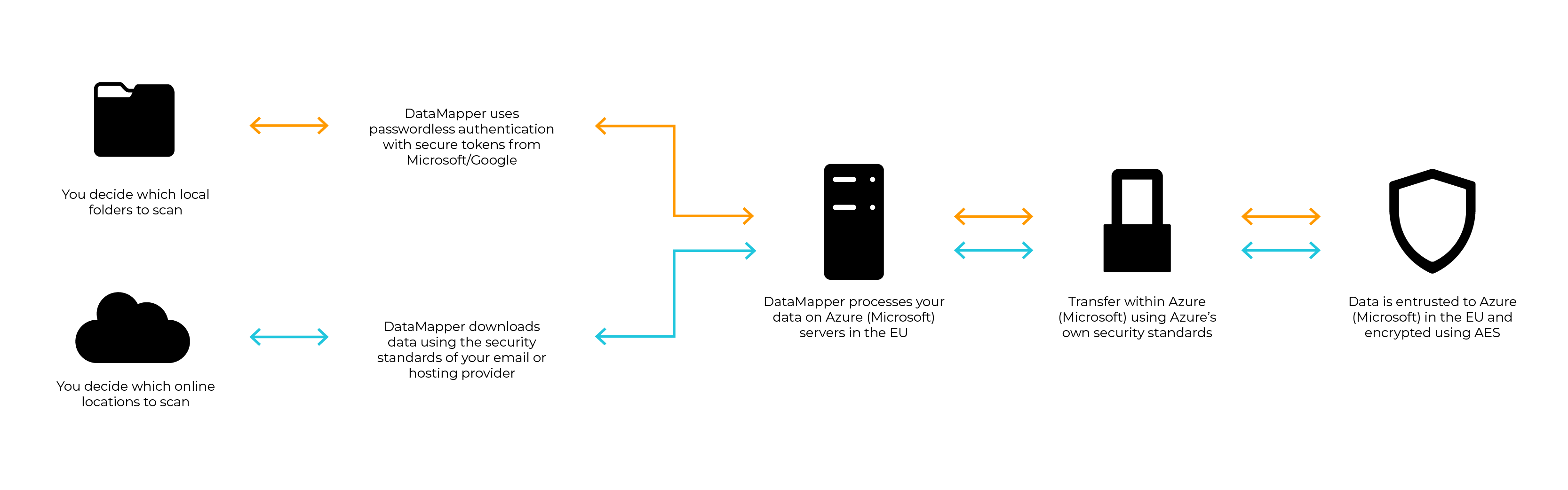
DataMapper data flow diagram
DataMapper can scan personal sensitive data from cloud solutions, desktop and network drives. Data can only be scanned, when the users choses the location and folders to scan and authenticates the scan using security tokes. Data is then moved to a secure tenant within a personal resource group where data is scanned and processed with AI/ML algoritms.
The scanned meta data (extracted data) is then transferred securely to a storage in your personal Azure tenant, where it will be used by DataMapper to visualize risks, enabling the user to clean up.
Data security measures
You control your team’s access
As the verified creator of an account, you get admin status and are the only one who can invite users to your team. You choose where the people you invite will have admin access of user access. Furthermore, admins can monitor a complete dashboard of everyone’s results, while users will only see their own results.
You stay in control
Each user chooses which locations and individual folders DataMapper can access and the user retains full control to manage data access over time.
No one else sees your results
All access to data is restricted with MFA and location access. We only access data upon request and with consent.
Security features
Your data is kept in the EU
We guarantee that your data will not leave the EU.
Frequent backups
We regularly make backups.
Access is logged
We log all access to files.
Users verified
Dedicated sign-up flow ensuring all user are verified.
Passwordless authentication
Secure tokens from Microsoft/ Google are securely transferred to our system for verification.
Encryption
All communication between your computer and our servers is encrypted using 2048-bit RSA encryption.
Certificates
Our servers are certified with X.509 certificates provided by WebTrust certified certificate authorities.
Servers
Our trusted third-party services from Azure use state-of-the-art access control. Server facilities are physically guarded.
Security patches
All servers are continuously kept up to date with Azure monitoring services, thus providing powerful end-to-end monitoring of our applications and components.
Data encrypted at rest
We use Azure private storage encrypted at rest with Azure managed AES 256 bit keys.
Data encrypted in transit
HTTPS in transit, TLS 1.5, Shared access signature.
Private tenant
By choosing Private tenant Datamapper will be hosted inside the company’s own Azure tenant.
Our ethical AI
As AI becomes more and more widely used, questions about its ethics arise. Indeed, anytime you use AI, you should ask if it is ethical and use it responsibly. That is what we do at Safe Online.
Ethical AI should adhere to well-defined ethical guidelines and protect fundamental values, including:
- Individual rights
- Privacy
- Non-discrimination
- Non-manipulation
DataMapper’s AI does not create ethical concerns, for the following reasons:
- DataMapper uses AI to quickly detect and classify the personal data you already store in your systems. It does not collect additional data from your customers in any way.
- You decide who to invite to DataMapper, and what access they will have to the information gathered. You can give a user access to only their own data storage (regular user); or give them access to data and statistics for the whole company.
- Once DataMapper’s AI finds sensitive data and shows it to you, it is up to you to decide what to do with it. DataMapper’s AI cannot be used for automated decision making and it does not alter or manipulate the data in any way.
How have we ensured that data scanned with AI is not stored and used for training by OpenAI or Microsoft?
Azure OpenAI ensures that:
- Prompts and generated content are not used to train OpenAI models.
- Data is not available to other customers or OpenAI.
- Data is not used to improve any Microsoft or third-party products or services.
- Your data remains exclusive to your use and is processed within the customer-specified geography.
How have we ensured that data processed with Azure OpenAI is not stored with Microsoft OpenAI or another third party?
Data processed by Azure OpenAI:
- Private tenant data is stored in the customer’s Azure subscription’s blob storage.
- Multitenant tenant data is stored in Safe Online’s Azure subscription’s blob storage for each customer.
- Data can be kept within the same region as the Azure resource.
- Data is not used for training OpenAI models.
- Customer-specific training can be fine-tuned by Safe Online and stored in Safe Online’s own models.
- Private tenant customers can verify data storage configurations using the Azure portal or Azure CLI.
Additionally, customers’ data is not used to train OpenAI models, and data remains under customer control in their Azure subscription.
For more details, you can refer to the Microsoft documentation.